AWS Identity Center (SSO)
This guide provides an overview of setting up AWS Identity Center (SSO) with ClickOps, detailing prerequisites and supported external identity providers. It explains how to integrate AWS SSO with providers like Okta, Azure AD, JumpCloud, and Google Workspace, including specific steps for configuring each.
How it Works
AWS Single Sign-On (AWS SSO) is a service that simplifies access management for AWS accounts and applications for managing your organization's workforce identity at scale across a multi-account AWS deployment. It enables users to sign in to AWS once and access multiple AWS accounts and applications without the need to re-enter credentials. To use it with an identity provider (e.g. such as Okta) for AWS SSO, administrators typically need to configure the integration within the AWS Management Console. This involves setting up a new AWS SSO instance, connecting it the IdP, and specifying the users or groups that should have access to AWS resources. AWS SSO provides logging and auditing capabilities, allowing organizations to track user access to AWS resources and monitor security-related events
-
SAML-Based Authentication
The integration between the IdP and AWS SSO relies on the Security Assertion Markup Language (SAML) for authentication and authorization. SAML enables the exchange of authentication and authorization data between Okta and AWS, allowing users to log in once to Okta and gain access to AWS resources without additional logins.
-
User Provisioning
AWS SSO can be configured to automatically provision and de-provision user accounts based on changes in the IdP directory. This helps keep user access in sync with changes made in the Okta environment.
-
AWS SSO Permission Sets
AWS SSO allows administrators to define fine-grained access policies, specifying which AWS accounts and services users from the IdP can access
-
Multi-Factor Authentication (MFA)
Organizations using Okta for authentication with AWS SSO can enhance security by enforcing multi-factor authentication (MFA) for added identity verification.
Once configured, users can experience single sign-on when accessing AWS resources. They log in to their IdP account and seamlessly gain access to AWS without needing to provide credentials again.
It's important to note that the specifics of the integration process may be subject to updates or changes, so it's recommended to refer to the official AWS documentation and Okta documentation for the most accurate and up-to-date information based on your current date.
Prerequisites
First, enable the AWS IAM Identity Center (successor to AWS Single Sign-On) service in the aws-admin account. This is the account where the aws-sso component will be deployed.
- Identity Center Prerequisites
- 1. Create Super-Admin-User
- 2. Enable AWS Organizations
- 3. Enable IAM Identity Center
-
1. AWS Account Setup
- An AWS account not part of AWS Organizations:
aws-admin - Go to the AWS IAM console and create a new user:
super-admin-user-
Provide user access to the AWS Management Console - optional>>I want to create an IAM user - Click
Next: Permissions to continue to the next step. ClickAttach policies directlyand chooseAdministratorAccess. - Click Create User.
- Click on the
Email sign-in instructionslink to receive the sign-in link.
-
- An AWS account not part of AWS Organizations:
-
2. Enable AWS Organizations
- Navigate to the
aws-adminaccount in the AWS Web Console -
EnableAWS Organizations
- Navigate to the
-
3. Enable IAM Identity Center:
- Go to AWS IAM Identity Center (successor to AWS Single Sign-On). Select your primary region:
ap-southeast-2 -
Enablethe service
- Go to AWS IAM Identity Center (successor to AWS Single Sign-On). Select your primary region:
Once enabled, IAM Identity Center creates a service-linked role in all accounts within the organization in AWS Organizations. IAM Identity Center also creates the same service-linked role in every account that is subsequently added to your organization. This role allows IAM Identity Center to access each account's resources on your behalf.
Configure your Identity Provider
These are the instructions for the most common Identity Providers. Alternatives are available, but the steps may vary depending on the provider.
It's important to note that the specifics of the integration process may be subject to updates or changes, so it's recommended to refer to the official AWS documentation and respective IdP documentation for the most accurate and up-to-date information based on your current date.
For providers not included in the following section, please follow the AWS documentation for setting up an IdP integration with AWS. This list includes Azure AD, CyberArk, OneLogin, and Ping Identity.
- 🛡️ Okta with SSO
- Microsoft 365
- GSuite and Other External IdPs
- JumpCloud
Okta is a common business suite that has an active director to manage users and permissions. We can utilize this to login to AWS by leveraging Applications that are used to sign in to things from your Okta Account.
Setup Okta with AWS Identity Center
⛑️ Your organization might be already managing workforce identity in Microsoft Active Directory or a standards-based identity provider such as Okta Universal Directory or Azure AD. In these situation, you can integrate these external identity providers (IDP) with AWS IAM Identity Center to provide a unified administration experience to define, customize, and assign fine-grained access. In this section, you will configure an Okta Universal Directory as the external Identity Provider (IDP) with AWS IAM Identity Center.
- 🛡️ Create an Okta account
- 🛡️ Create Users/Groups in Okta
- 🛡️ Create IAM Identity Center Application in Okta
- ⛅️ Configure/Change the Identity Source in Identity Center
- 🛡️ Configure Okta SSO
- 🛡️ Configure Provision/SCIM in Okta
- 🛡️ Assign User/Groups to IAM Identity Center Application in Okta
- ⛅️ Assign access to AWS Accounts through Permission Sets
- 🛡️⛅️ Test access
- 1. 🛡️ Create Account
- 2. 🛡️ Create Users/Groups in Okta
- 3. 🛡️ Create SSO Application
- 4. Change Identity Source
- 5. 🛡️ Configure Okta SSO
- 6. 🛡️ Configure Provision/SCIM
- 7. 🛡️ Assign User/Groups to AWS-SSO
- 8. ⛅️ Permission Sets
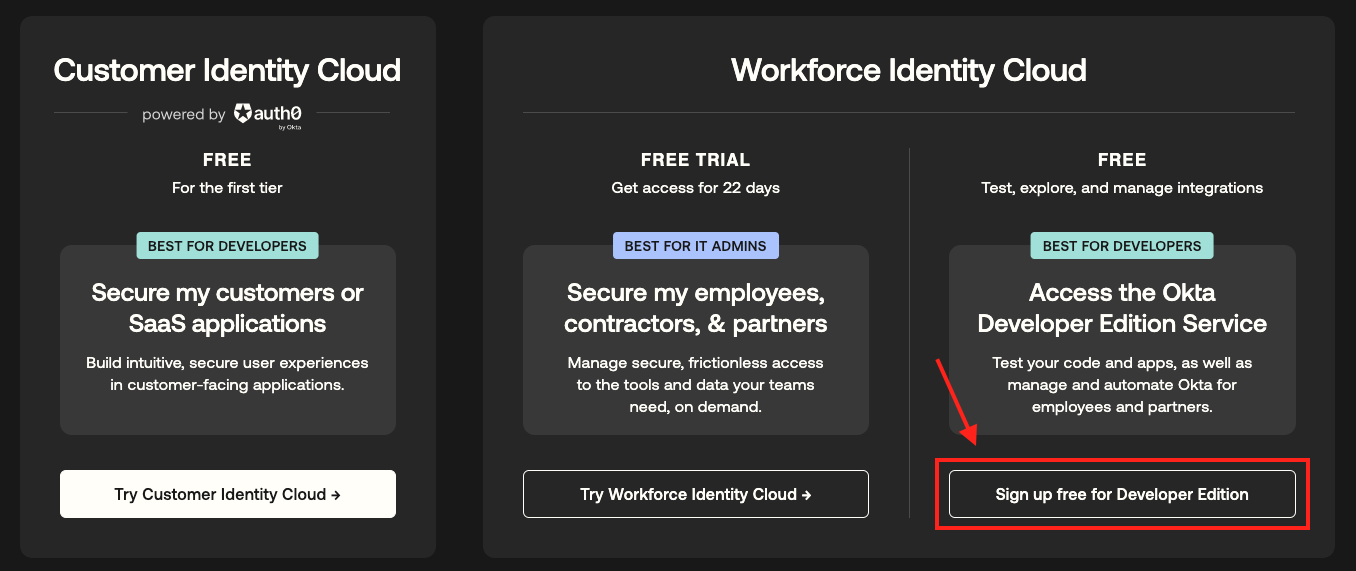
- Click here to create your free Okta account: No credit card is required.
- Select
Sign up free for Developer Edition.- You will receive an Email. Click on the link to activate your account.
- Set the password (and MFA) of your Okta Account and you are ready to go.
-
1. Create Groups in Okta: Let's create a group
Okta-AWS-PowerUserAccessin Okta- Navigate to the
Directorysection on the left-hand side of the page. - Choose Groups
- Click on
Add groupbutton Okta Add Group page - In the Add Group dialog:
- Name - Provide the name of the group:
Okta-AWS-PowerUserAccess - Description (optional) - Provide the description for the group:
Enables PowerUserAccess to an AWS Account. - Click on the
Savebutton Okta Add Group page
- Name - Provide the name of the group:
- Navigate to the
-
2. Create People
- Navigate to the Directory section on the left-hand side of the page.
- Choose
People - Click on
Add personbutton Okta Add User page - In the Add Person dialog:
- Provide the first name:
Nhat-Thanh - Provide the Last name:
Nguyen - Provide the username:
[email protected] - Leave Primary email as entered
- Choose the Groups as
Okta-AWS-PowerUserAccess - For Password, Choose
I will set passwordand enter a password - Uncheck the
User must change password on first login
- Provide the first name:
- Click on the
Savebutton Okta Add User page
- Navigate to the Applications section on the left-hand side of the page.
- Click Browse App Catalog
- Search for
AWS IAM Identity Centerand click Add Integration - Keep the default settings of App Label (
AWS IAM Identity Center) and Application Visibility. In the application Wizard page for the Application: Click Done button - Go to Sign On and Copy information from the SAML Metadata section, this will be used in AWS SSO. Under the SAML Signing Certificates section, from the Actions drop-down menu, right-click on View IDP metadata and save the link as
okta_metadata.xmlto a file locally.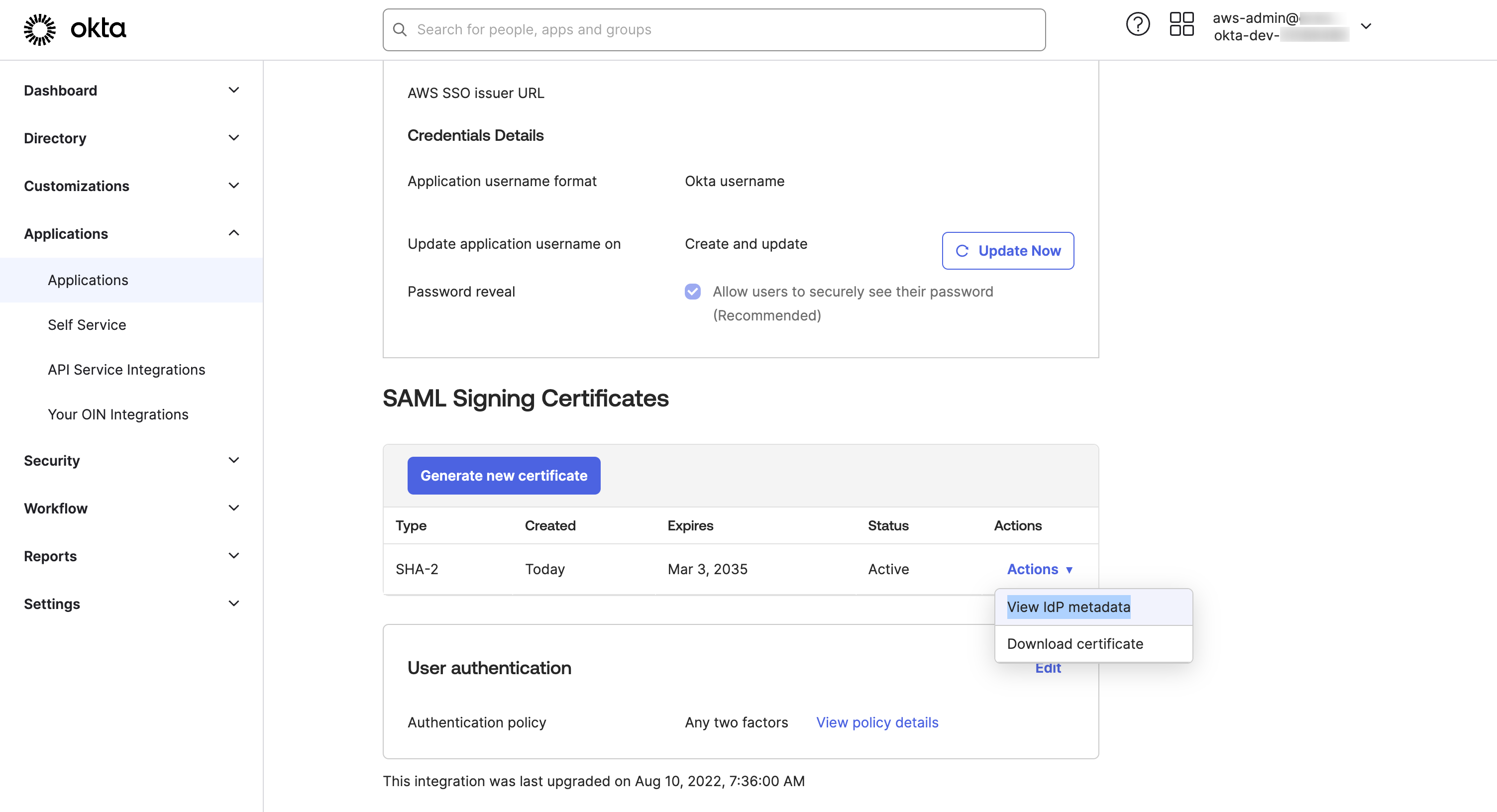
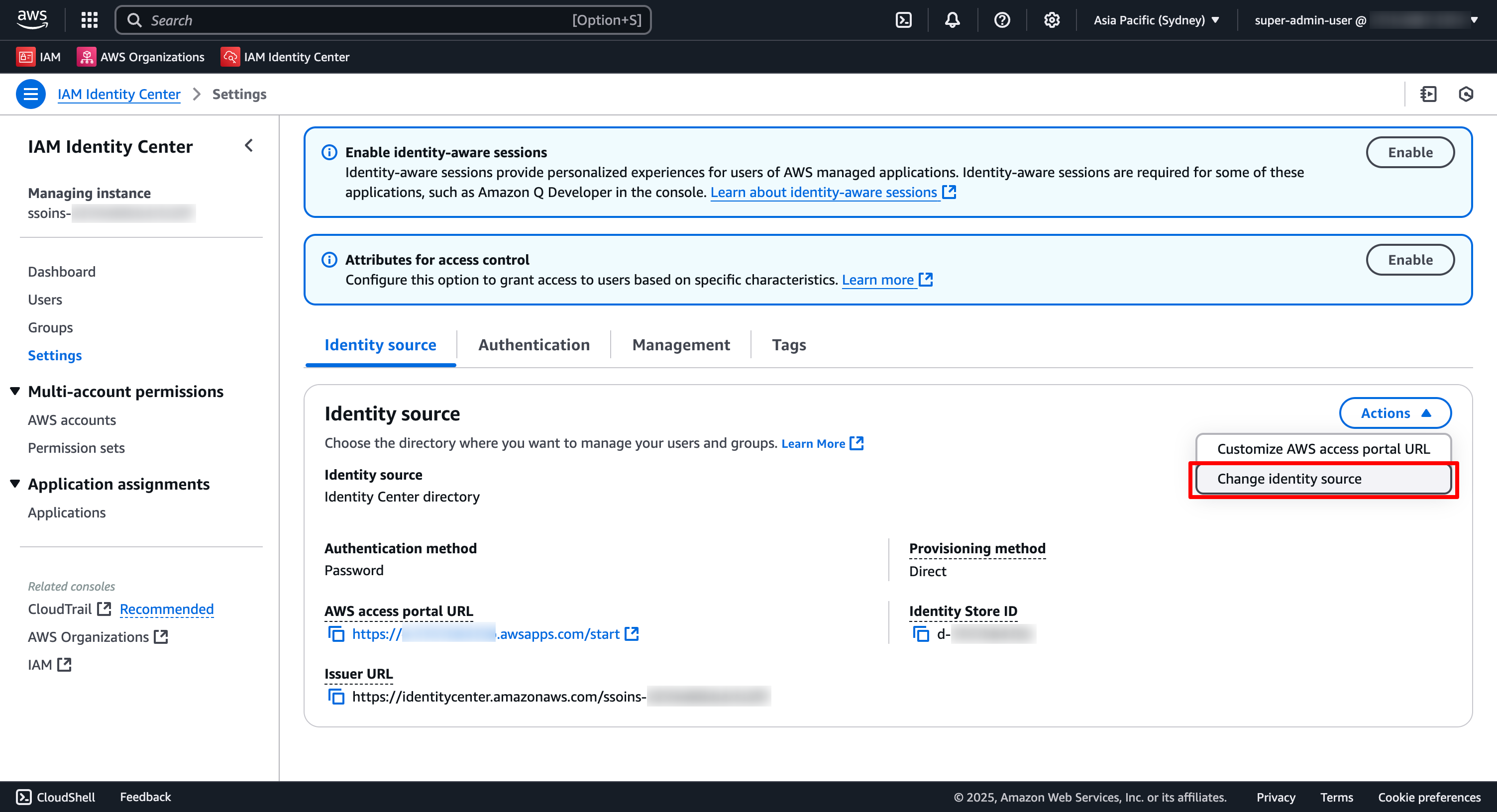
- Sign into Navigate to the IAM Identity Center Console under your management account
aws-admin|super-admin-user| AWS Regionap-southeast-2 - Select Settings from the left menu. In the Setting page, under Identity source tab, Choose Change Identity Source from Actions drop-down menu
- In the Choose identity source page:
Choose External identity provider, and Click Next
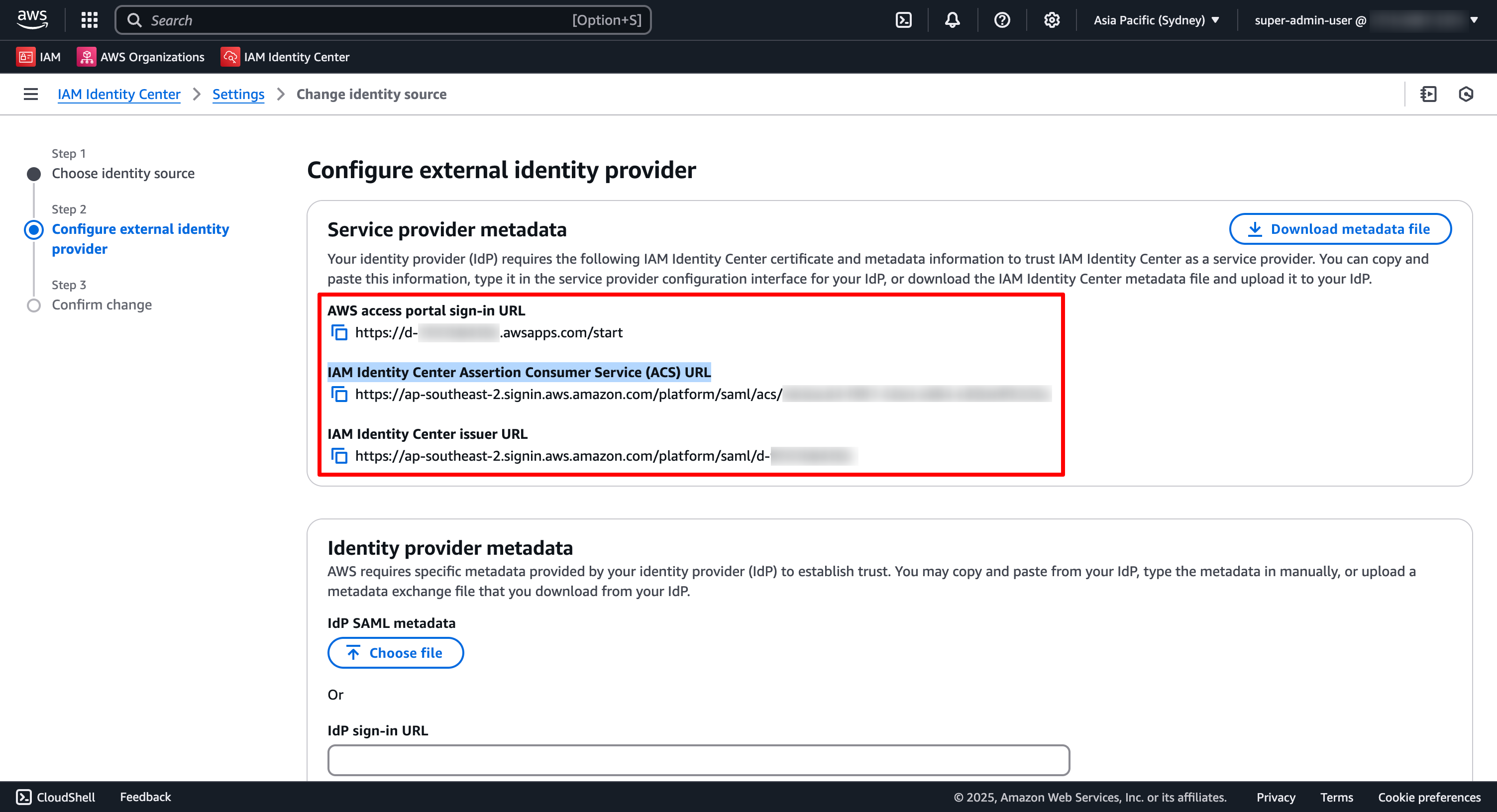
In the Configure external identity provider page: Make a Make a copy of the IAM Identity Center Assertion Consumer Service (ACS) URL, and IAM Identity Center issuer URL values in the Service provider metadata section. These values will be used later on.
- In the Identity provider metadata section: Click on the Choose file button under IdP SAML metadata label and choose the
okta_metadata.xmlwe saved in the previous step; then Click Next In the Confirm change page: TypeACCEPTand Click on Change identity source
Configure Okta AWS IAM Identity Center >> Sign On configuration:
In the AWS Single Sign-on App page,
- Navigate to the Sign On Tab, click on the Edit button
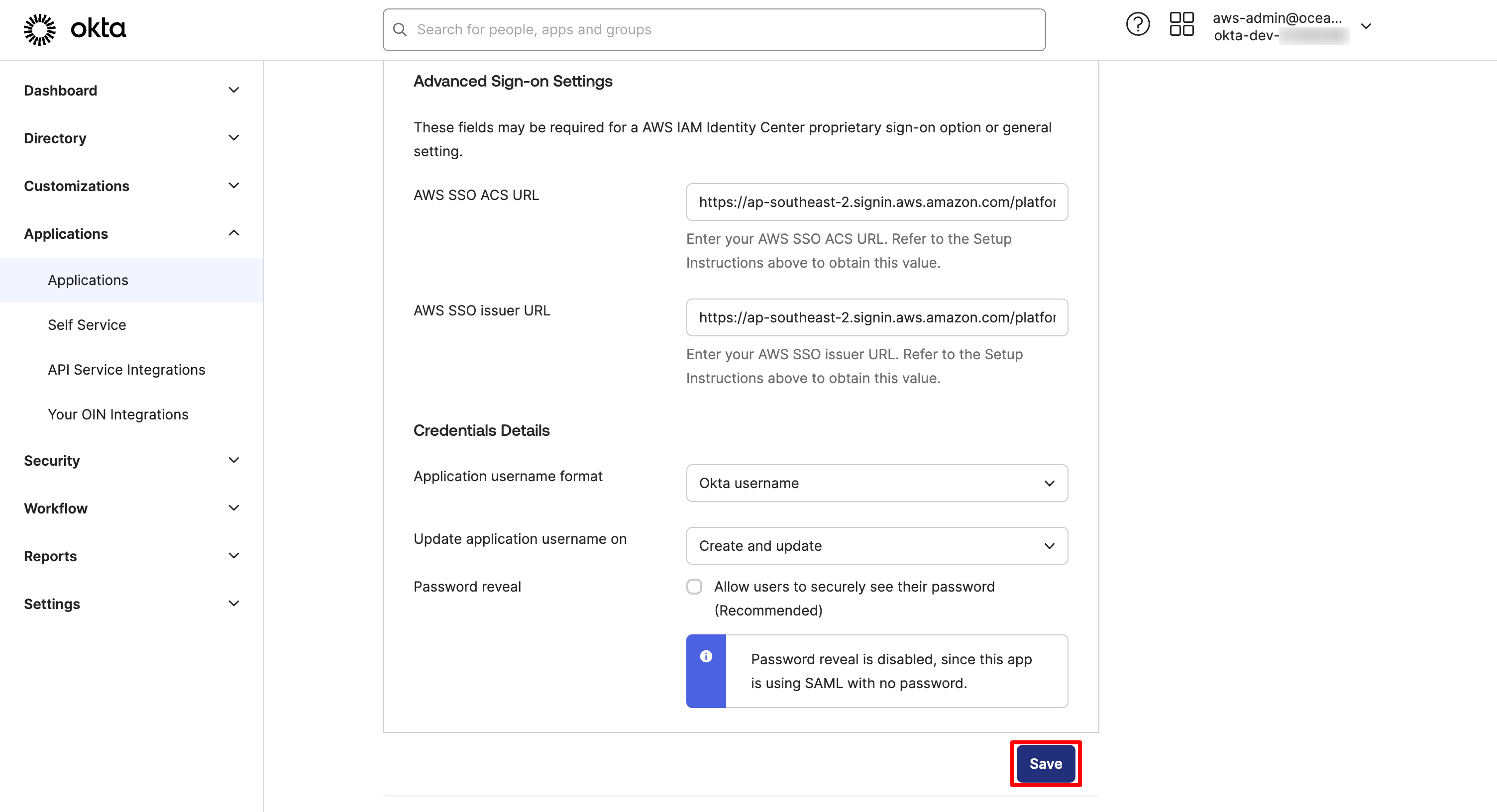
- Under the Advanced Sign-on Settings section
- Enter your AWS SSO ACS URL:
IAM Identity Center Assertion Consumer Service (ACS) URLand AWS SSO issuer URL:IAM Identity Center issuer URLvalues you made a copy in Step 4 in previous section - Leave the Credentials Details Configuration as to default selections
- Click Save
- Enter your AWS SSO ACS URL:
In this section, you will configure SCIM to enable the users and groups from Okta to be automatically sync'ed into the Identity Center.
6.1. ⛅️ In AWS Identity Center Console:
- Navigate to the IAM Identity Center Console
- Select Settings from the left menu
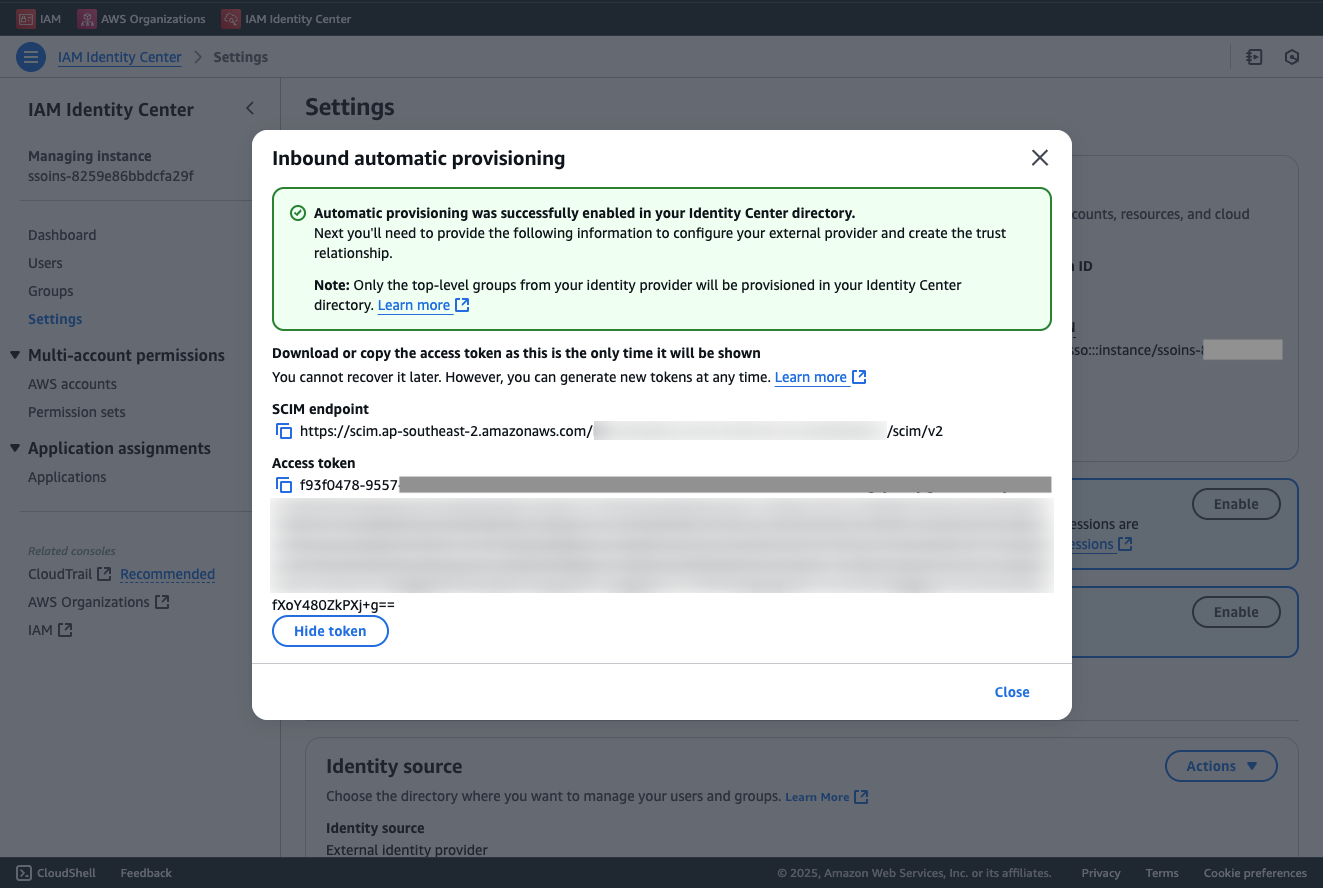
- In the Setting page, Click on
Enablewithin the Automatic provisioning info block - In the Inbound automatic provisioning dialog, Copy the SCIM endpoint and the Access token, we will use it to configure it within the Okta admin dashboard.
6.2. 🛡️ In Okta Admin Dashboard:
- Navigate to the Provisioning tab within the Okta's IAM Identity Center Application
- Click on Configure API Integration Okta SSO SCIM page:
Select the checkbox for Enable API integration.
Provide the Base URL value with the
SCIM endpointcopied from Step 6.1 in the previous section. When you copy the URL, make sure there is no “/” at the end or link validation in Okta will fail. Provide API Token value with theAccess tokencopied from Step 6.1 in the previous section. Click Test API Credentials to test the end-point. You will see a green banner with message "AWS IAM Identity Center was verified successfully!" Click Save to Save the configuration Okta SSO SCIM page.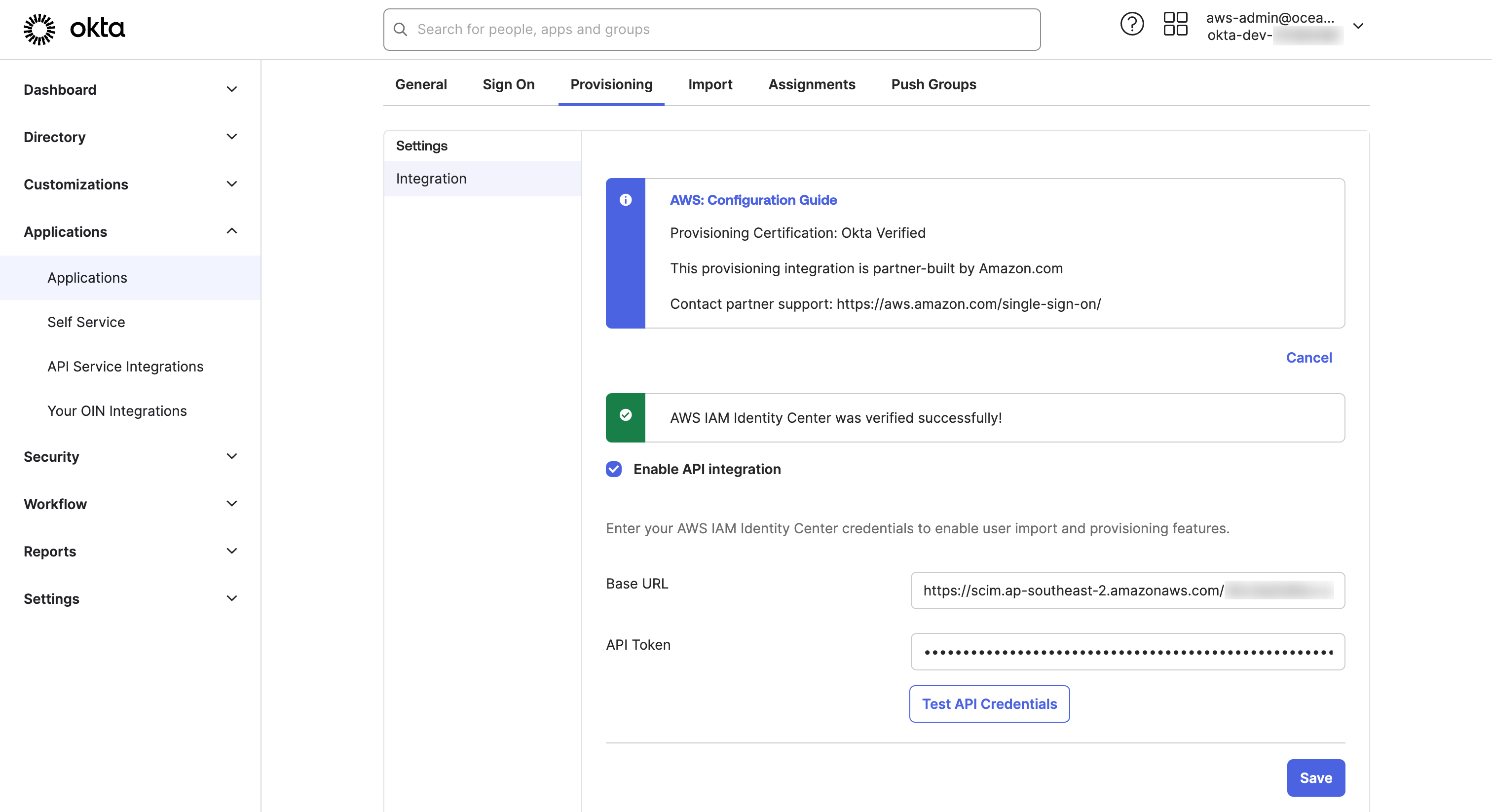
- In the Provisioning tab make sure that To App is selected.
Click on Edit
Select Enable for
Create Users,Update User Attributes, andDeactivate Users. Click on Save.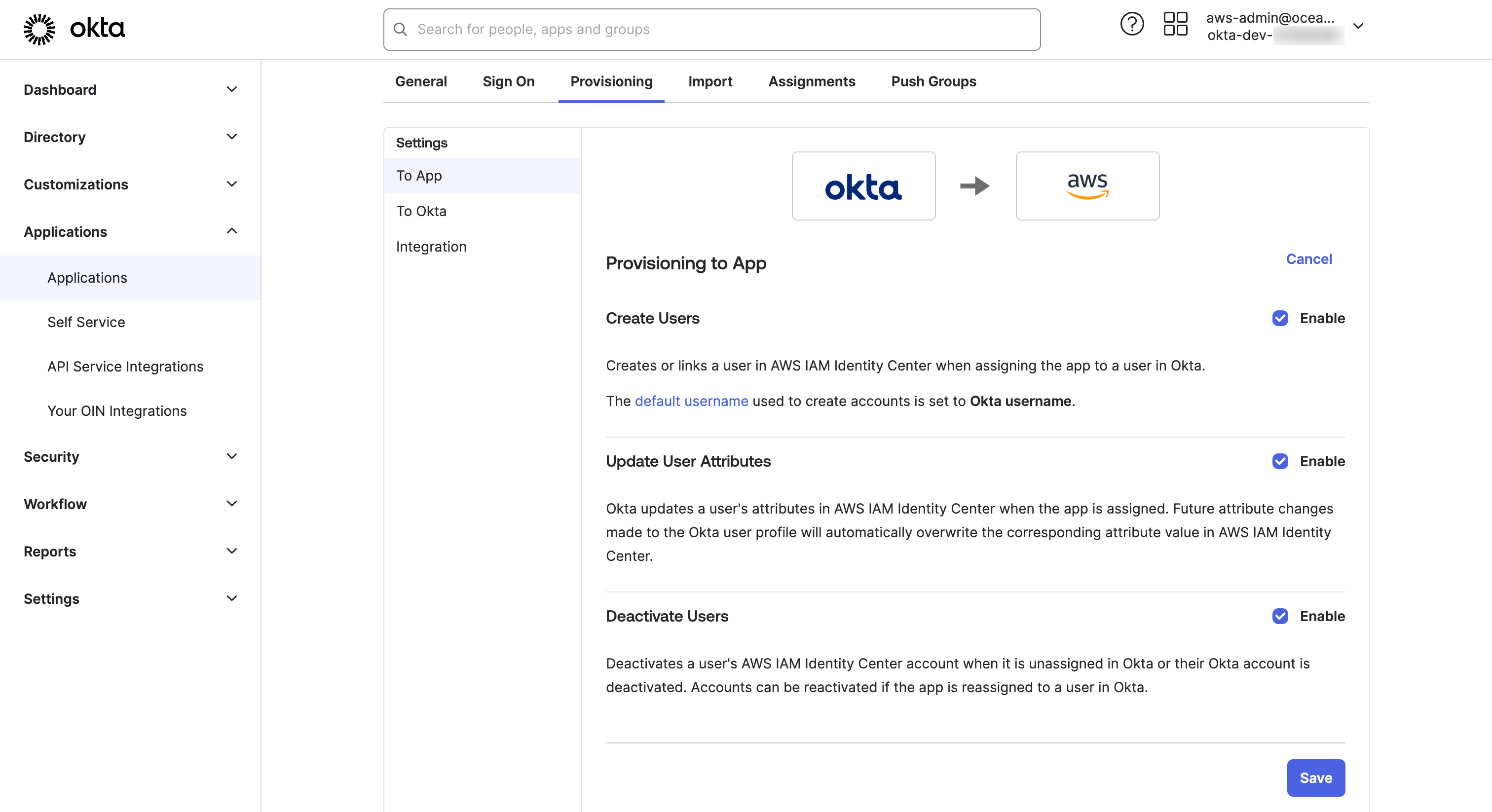
To allow users access via SSO, we must assign them to the IAM Identity Center Application in Okta. As soon as you assign a user or group, Okta will call in the background the APIs to create the user in IAM Identity Center. If you change a mapped attribute e.g. FirstName, Okta will update the attribute also in IAM Identity Center. If you unassign a user, it will be deactivated in IAM Identity Center. Okta takes care of the full user life-cycle management.
- 🛡️ In Okta admin dashboard >>
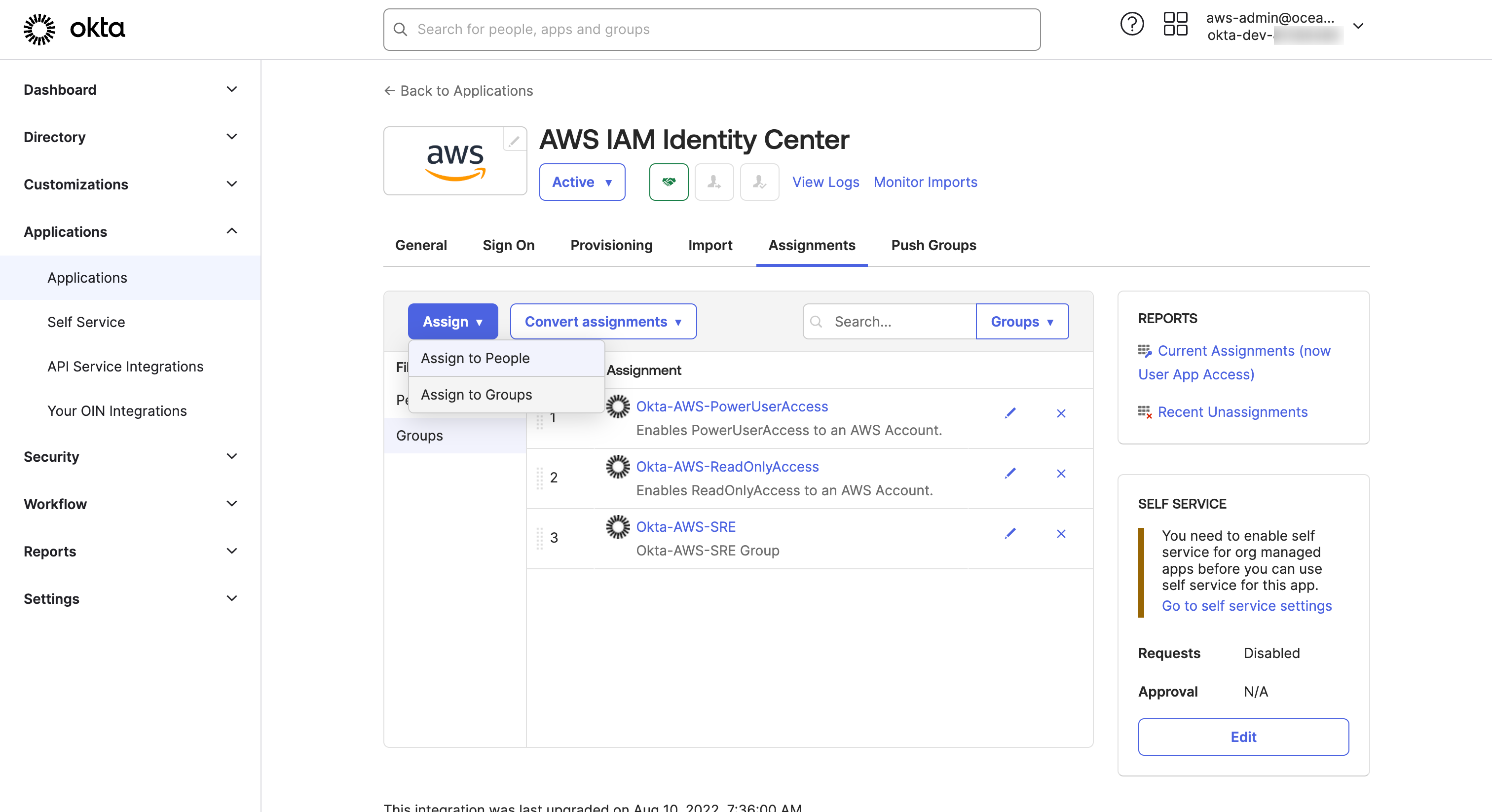
AWS IAM Identity CenterOkta-Applications, Go to Assignment tab and
- Click on Assign to Groups within the Assign pull-down button Okta assignment page
- Choose
Okta-AWS-PowerUserAccessgroup and click Assign Okta assignment page. A dialog will appear to do additional attribute mapping per group. No changes are required, select Save and Go Back - Click Done on Assignment dialog Okta assignment page
IAM Identity Center doesn’t know about Okta groups yet. We will use the groups to map the Permission Sets in IAM Identity Center. Let’s push the groups and their memberships to IAM Identity Center.
- 🛡️ In Okta admin dashboard, Go to Push Groups tab and
- Click Find groups by name from the Push Groups pull-down button Okta push groups page.
- Search for
Okta-AWS-PowerUserAccessgroup and Click on Save - After few seconds, you should see the Push Status as
Activein Push Groups to AWS IAM Identity Center page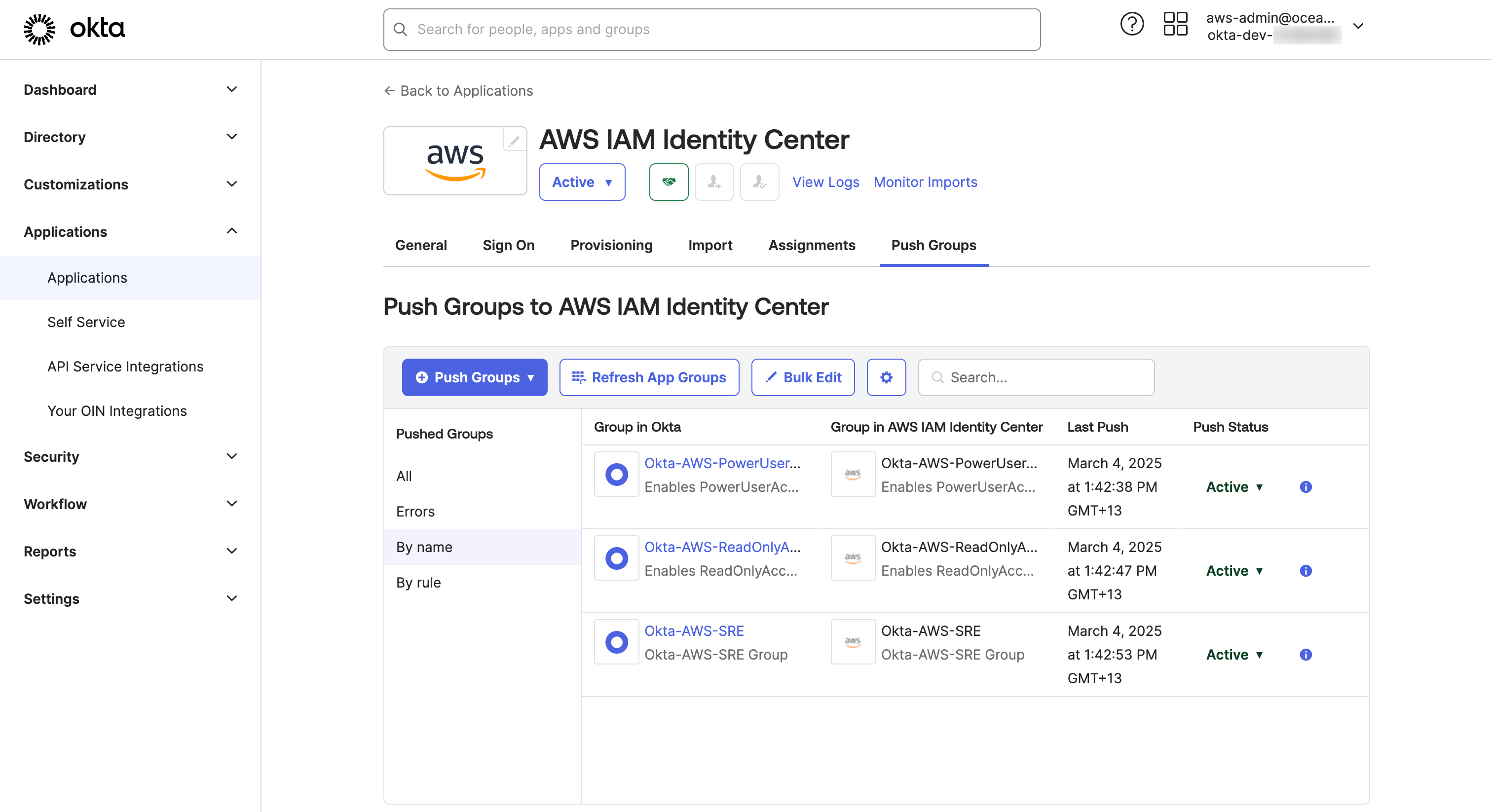
Let's validate the new
Okta-AWS-PowerUserAccessgroup is now synced into AWS IAM Identity Center
- ⛅️ Navigate to the IAM Identity Center Console
- Select Groups from the left menu
- In the Groups list page, validate that
Okta-AWS-PowerUserAccessgroups exists with Created by value asSCIMin IAM Identity Center Group list page.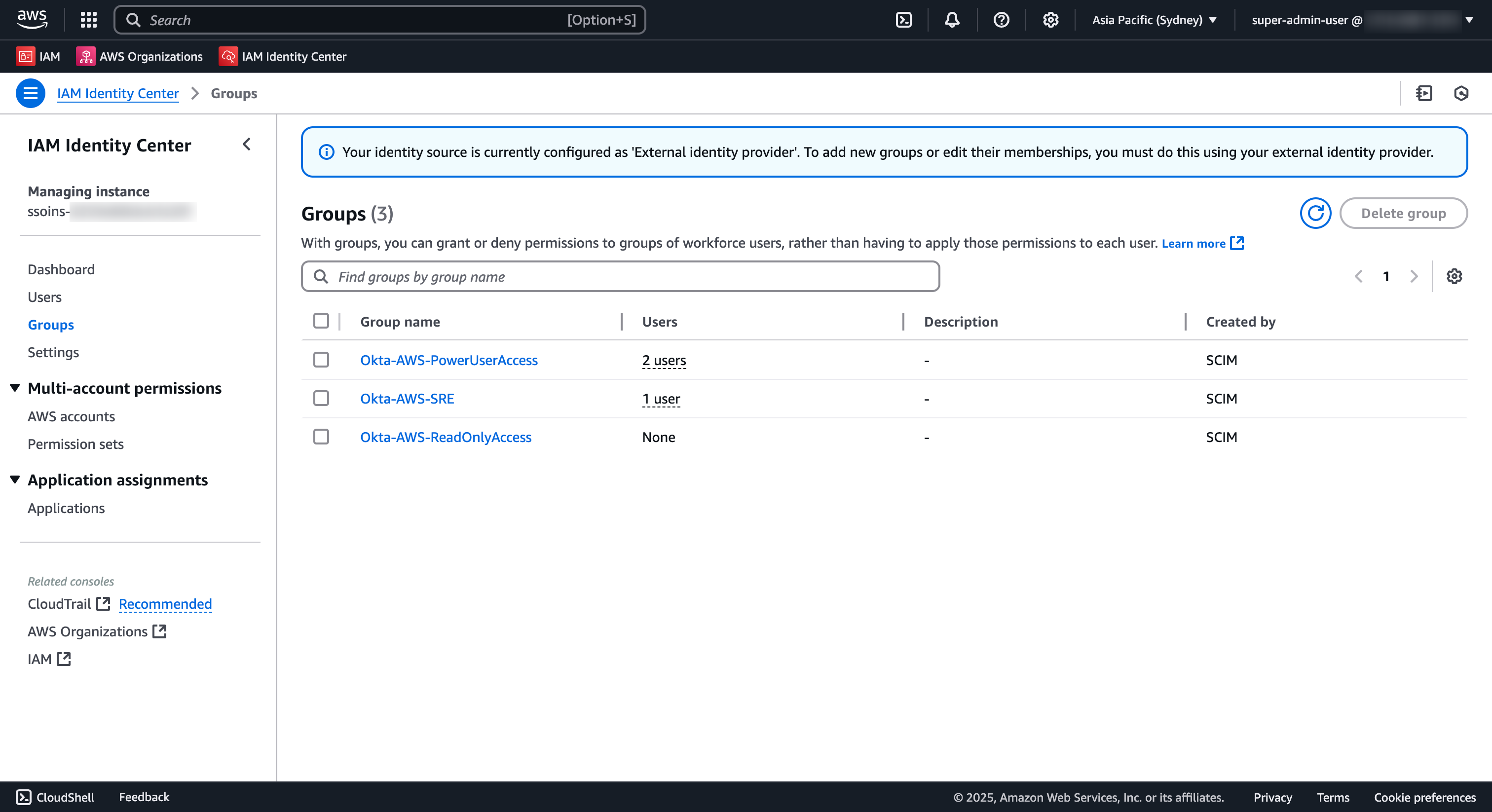
Create Permission Set with PowerUser permission
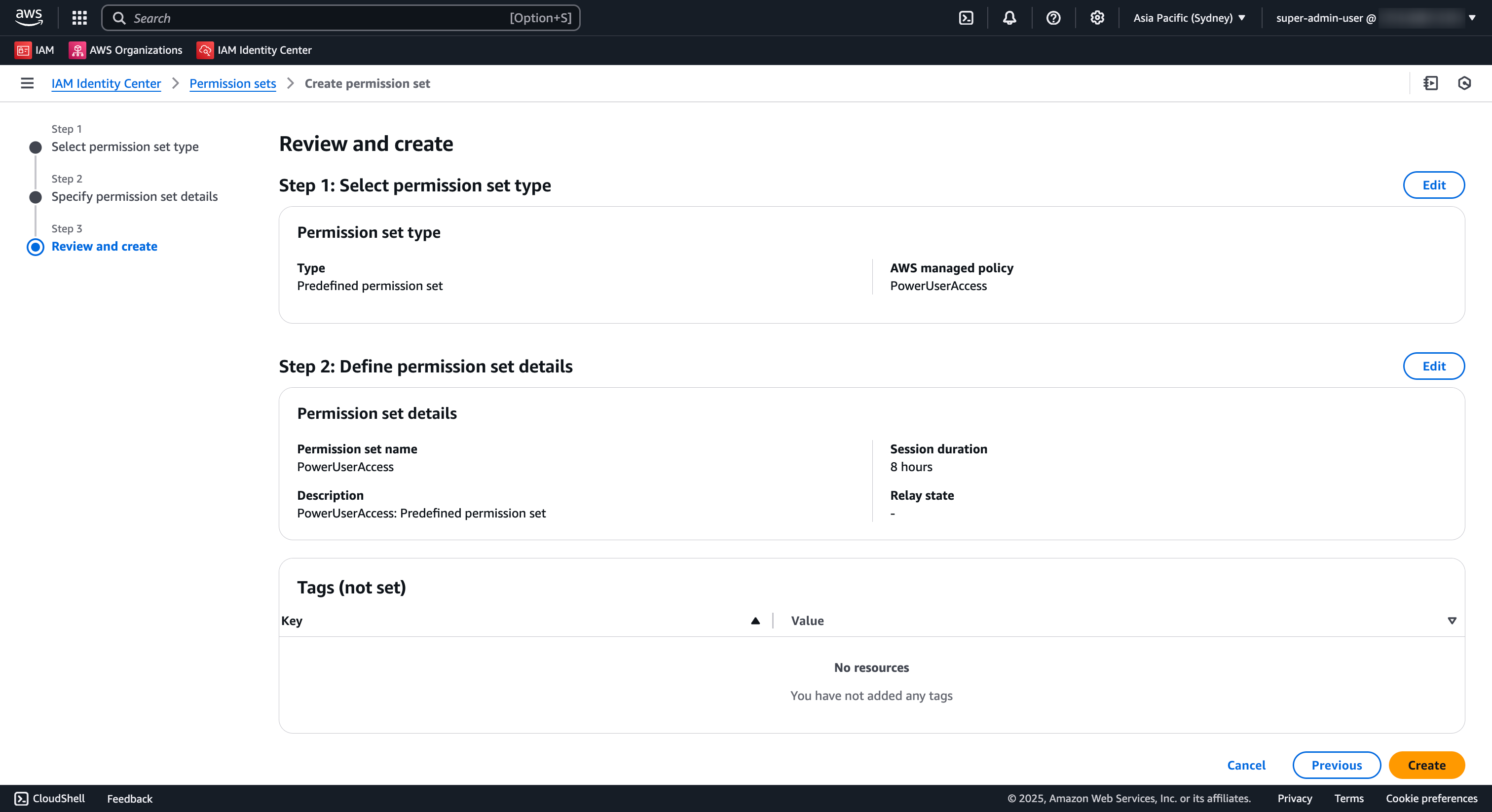
- Navigate to the IAM Identity Center Console
- Select Permission sets from the left menu
- Click Create permission set
- In the Select permission set type
- Choose
Predefined permission set - For Policy for predefined permission set, Choose
PowerUserAccess - Click Next
- In the Specify permission set details page
- Provide
PowerUserAccessas the Permission set name - Leave rest of the settings as default
- Click Next
- In the Review and create page:
- Review the configuration
- Click Create to create the permission set
Assign Permission Set to AWS Account
- Navigate to the IAM Identity Center Console, choose AWS accounts
- Choose an AWS account where you want to user to have access.
- Click Assign users or groups.
- In the Assign users and Group to AccountName page:
- Choose the
Okta-AWS-PowerUserAccessgroup - Click Next
- In Select permission sets page,
- Under Permission sets, select
PowerUserAccess - Click Next
- In Review and submit page:
- Review the information
- Click Submit
IAM Identity Center will now associate the User group with the Permission set and assign it to the select AWS Account(s). You should see a page with green banner like below.
9. 🛡️⛅️ Test Access
Now that we have everything configured, we can test the access to AWS with the proper permissions. You can start the test and login from Okta (IDP-initiated) or AWS
- Navigate to the IAM Identity Center Console
- Select Settings from the left menu
- Open the AWS access portal URL in a new browser, the URL should be of the format
https://d-xxxxxxxxxx.awsapps.com/start - This should navigate you to the Okta login page IAM Identity Center Portal page
- Once you provide the user credentials, on successful login , you should be navigated to the SSO portal page IAM Identity Center Portal page
- Navigate to the Management Console using the the
PowerUserAccessrole
⛅️ Cleanup Identity Center resources
- Navigate to the IAM Identity Center Console
- Choose the AWS Region you intend to configure the rule:
ap-southeast-2
- Select
Settingsfrom the left menu
- In the Setting page , choose
Managementtab - Click on the
Deletebutton under theDelete IAM Identity Center instanceconfiguration Settings management tab - Type the ^^instance id^^ in the text box and click on the Confirm button in Dialog window Confirm delete settings
Microsoft 365 (formerly known as Office 365) can be used as an identity provider for AWS (Amazon Web Services) through a feature called AWS Single Sign-On (AWS SSO).
AWS SSO allows organizations to centralize identity management and provide users with seamless access to AWS resources using their existing Microsoft 365 credentials.
Setup Microsoft 365
-
Under https://aad.portal.azure.com/#allservices/category/All go to Enterprise Applications --img src="-assets-refarch-screen-shot-2023-01-13-at-8.33.13-am.png" />
-
Click New Application
-
Choose the right application, for SSO it’s AWS IAM Identity Center (successor to AWS Single Sign-On) --img src="-assets-refarch-screen-shot-2023-01-13-at-8.36.16-am.png" />
-
Click Create, default options are fine
-
On the Left Panel Click Single sign-on, then download the XML File by Pressing the Button on step 5 Set up AWS IAM Identity Center (successor to AWS Single Sign-On) --img src="-assets-refarch-screen-shot-2023-01-13-at-8.41.28-am.png" /> The Metadata file downloaded will need to be given to the 1xOps team, as it is used in AWS for setting up SSO.
-
Similarly, in Jumpstarts the DevOps Accelerator Team will give you an XML file from AWS SSO that contains metadata. Upload this by clicking the Upload metadata file button. --img src="-assets-refarch-screen-shot-2023-01-13-at-8.47.03-am.png" />
-
SAVE
Automatic Provisioning
-
DevOps Accelerator team will provide a URL and secret via 1Password
-
Go to Your App for Single Sign On, on the left Panel go to Provisioning
-
Set the mode to Automatic and Paste the Values provided into the Admin Credentials Section --img src="-assets-refarch-screen-shot-2023-01-13-at-8.53.55-am.png" />
For non-explicitly supported Identity Providers, such as GSuite, set up the app integration with a custom external identity provider. The steps may be different for each IdP, but the goal is ultimately the same.
GSuite does not automatically sync both Users and Groups with AWS Identity Center without additional configuration! If using GSuite as an IdP, considering deploying the ssosync tool.
Please see our aws-ssosync component for details!
-
Open the Identity account in the AWS Console
-
On the Dashboard page of the IAM Identity Center console, select Choose your identity source
-
In the Settings, choose the Identity source tab, select the Actions dropdown in the top right, and then select Change identity source
-
By default, IAM Identity Center uses its own directory as the IdP. To use another IdP, you have to switch to an external identity provider. Select External identity provider from the available identity sources
-
Configure the custom SAML application with the Service provider metadata generated from your IdP. Follow the next steps from your IdP, and then complete this AWS configuration afterwards
-
Open your chosen IdP
-
Create a new SSO application
-
Download the new app's IdP metadata and use this to complete step 5 above
-
Fill in the Service provider details using the data from IAM Identity Center, and then choose Continue. The mapping for the data is as follows:
For ACS URL, enter the IAM Identity Center Assertion Consumer Service (ACS) URL.
For Entity ID, enter the IAM Identity Center issuer URL.
Leave the Start URL field empty.
For Name ID format, select EMAIL. -
If required for the IdP, enable the application for all users
-
Finally, define specific Groups to match the given Group names by the aws-sso component (
stacks/catalog/aws-sso.yaml). In the default catalog, we define four Groups:DevOps,Developers,BillingAdmin, andEveryone
If set up properly, Users and Groups added to your IdP will automatically populate and update in AWS.
Additional IdP specific setup reference can be found here:
JumpCloud is a cloud-based directory service that provides secure, frictionless access to AWS resources. It can be used as an identity provider for AWS (Amazon Web Services) through a feature called AWS Single Sign-On (AWS SSO).
Follow the JumpCloud official documentation for setting up JumpCloud with AWS IAM Identity Center:
Integrate with AWS IAM Identity Center
The official AWS documentation for setting up JumpCloud with AWS IAM Identity Center is not accurate. Instead, please refer to the JumpCloud official documentation
- Identify: NIST Cyber Security Framework (CSF) Functions
- Directive: Cloud Adoption Framework (CAF) Components